Fourth Spy Unearthed in U.S. Atomic Bomb Project →
The world's first atomic bomb was detonated on July 16, 1945, in the New Mexican desert — a result of a highly secretive effort code-named the Manhattan Project, whose nerve center lay nearby in Los Alamos. Just 49 months later, the Soviets detonated a nearly identical device in Central Asia, and Washington's monopoly on nuclear arms abruptly ended.
How Moscow managed to make such quick progress has long fascinated scientists, federal agents and historians. The work of three spies eventually came to light. Now atomic sleuths have found a fourth. Oscar Seborer, like the other spies, worked at wartime Los Alamos, a remote site ringed by tall fences and armed guards. Mr. Seborer nonetheless managed to pass sensitive information about the design of the American weapon to Soviet agents.
[...]
His role "has remained hidden for 70 years," write Harvey Klehr and John Earl Haynes in the current issue of Studies in Intelligence, the C.I.A.'s in-house journal; their article is titled "On the Trail of a Fourth Soviet Spy at Los Alamos."
It got better two months later as it was learned that the spy, Oscar Seborer, had the most intimate working knowledge of the American bomb's construction of all the spies. He worked on the explosive trigger mechanism. His codename? Godsend.
Michael Tilson Thomas was once the 'bad boy of classical music.' Now, at 74, he still conducts with childlike delight. →
Michael Tilson Thomas is 74 years old. In conductor years, that's young.
He wears his elder-statesman mantle lightly, even with a kind of incredulity. He's "MTT," music director of the San Francisco Symphony, co-founder of the New World Symphony in Florida, sometime-leader of dozens of major orchestras around the world, expert communicator, breaker-down of musical genres and still, at bottom, the youngest-ever conductor of the Boston Symphony Orchestra, of whom Leonard Bernstein once said, "He reminds me of me at that age." Thomas has been famous for so long, and boyish for so long, that he hasn't had to struggle to attain the one or ever entirely abandon the other.
It has been amazing to attend the San Francisco Symphony this season. Absolutely phenomenal works and inspiring energy, even all the way up in my cheap seats.
Total Surveillance Is Not What America Signed Up For →
The incongruity between the robust legal regime around legacy methods of privacy invasion and the paucity of regulation around more comprehensive and intrusive modern technologies has come into sharp relief in an investigation into the location data industry by Times Opinion. The investigation, which builds on work last year by The Time's newsroom, was based on a dataset provided to Times Opinion by sources alarmed by the power of the tracking industry. The largest such file known to have been examined by journalists, it reveals more than 50 billion location pings from the phones of more than 12 million Americans across several major cities.
By analyzing these pings, our journalists were able to track the movements of President Trump's Secret Service guards and of senior Pentagon officials. They could follow protesters to their homes and stalk high-school students across Los Angeles. In most cases, it was child's play for them to connect a supposedly anonymous data trail to a name and an address — to a real live human being.
The collection, aggregation, and sale of personal location data needs to be be banned. Location is yet another way in which we've become the product technology companies are selling.
I was a '60s socialist. Today's progressives are in danger of repeating my generation's mistakes. →
For the foreseeable future, though, if the left wants to create the political majority […], it will have to frame its positions in a vernacular that most Americans can understand. It will also have to draw a sharp distinction between the positions it deems essential for "big, structural change" and those that can be delegated to communities to calibrate and debate. The new left of the '60s failed in this mission. We didn't just dream big; we ascended into the realm of fantasy and visible sainthood. Today's left will need to learn from our mistakes.
Failing to moderate and propose practical, bipartisan policies will mean the left's coalition will be unable to effectively wield political influence.
The CIA secretly bought a company that sold encryption devices across the world. Then its spies sat back and listened. →
[…] Crypto AG was secretly owned by the CIA in a highly classified partnership with West German intelligence. These spy agencies rigged the company's devices so they could easily break the codes that countries used to send encrypted messages.
The decades-long arrangement, among the most closely guarded secrets of the Cold War, is laid bare in a classified, comprehensive CIA history of the operation obtained by The Washington Post and ZDF, a German public broadcaster, in a joint reporting project.
Absolutely fascinating.
California Police Have Been Illegally Sharing License Plate Reader Data →
Some of California's largest police departments have been collecting millions of images of drivers' license plates and sharing them with entities around the country—without having necessary security policies in place, in violation of state law, according to a newly released state audit.
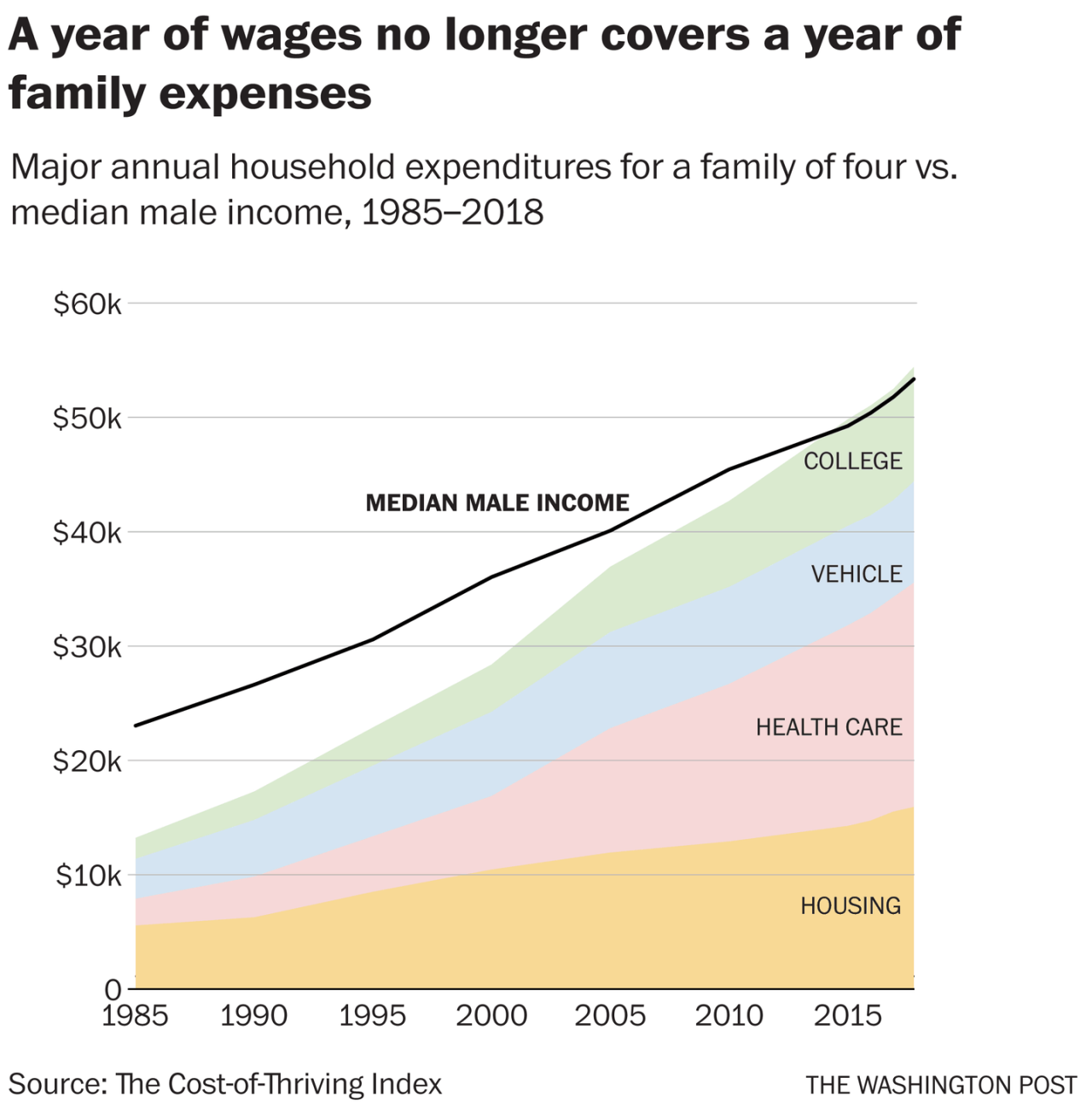
Lead author Oren Cass distills it as follows: "In 1985, the typical male worker could cover a family of four's major expenditures (housing, health care, transportation, education) on 30 weeks of salary," he wrote on Twitter last week. "By 2018 it took 53 weeks. Which is a problem, there being 52 weeks in a year."
(via This chart is the best explanation of middle-class finances you will ever see - The Washington Post)
How 'The Mandalorian' and ILM invisibly reinvented film and TV production →
This is so cool. See also https://ascmag.com/articles/the-mandalorian.
Opinion | Quiz: Let Us Predict Whether You're a Democrat or a Republican →
Tell us a few details about you and we'll guess which political party you belong to. It shouldn't be that simple, right? We're all complex people with a multiplicity of identities and values. But the reality is that in America today, how you answer a handful of questions is very likely to determine how you vote.
Regardless of how you vote, make sure you vote. Super Tuesday is next week! If you don't know if or how you can vote, start at https://vote.gov.
There are people who believe that law, morality, traditions and institutions are at least as important to the preservation of freedom as the will of the people. Such people are called conservative. What Republicans are now doing with their lock step opposition to impeachment — and with their indifference to the behavior that brought impeachment about — is not conservative. It is the abdication of principle to power.
— Bret L. Stephens, The Conservative Case for Impeachment — and Removal